Conventional Encryption Is a Term Used to Describe ______________ Encryption
Since ancient times various methods have been used to transform readable contentknown as plaintextinto a non-readable form. Conventional methods are broadly divided into two classes.

Symmetric Vs Asymmetric Encryption What Are Differences Cryptography Symmetric Cryptography Cyber Security Awareness
Perceptual encryption is a term used to describe various applications of encryption methods intended for audio speech image and video data.

. It was the only type of encryption in use prior to the development of public-key encryption. The encryption algorithm is a cryptographic algorithm that inputs plain text and an encryption key and produces a ciphertext. T or F The two important aspects of encryption are to verify that the contents of the.
Terms in this set 30 T or F Public key algorithms are useful in the exchange of conventional encryption keys. The term encryption is commonly used to describe techniques that are intended to protect information from unauthorized access. It remains by far the most widely used of the two types of encryption.
It is still much preferred of the two types of encryption systems due to its simplicity. For example DES Triple DES algorithms MARS by IBM RC2 RC4 RC5 RC6. The decryption key is kept private hence the private key name while the encryption key is shared publicly for anyone to.
One key is used for encryption and a different key is used for decryption. It may be considered as intentionally degrading the quality of the multimedia. Modern protocols will use a private key for encryption and a different public key for decryption.
Encryption is used in the 21st century to protect digital data and information systems. The universal technique for providing confidentiality for transmitted data is conventional encryption. ____ Authenticated encryption _____ is a term used to describe encryption systems that simultaneously protect confidentiality and authenticity integrity of communications.
Converting the non-readable text into readable text which anyone can understand. Asymmetric two key or public key encryption. Private key encryption is used to produce digital signatures which provide an enhanced form of message authentication.
Only 13 said they did not have a strategy at all. Converting the text from readable format to nonreadable format to secure the conversation between two parties or from the unauthorized person. The key is used for both encryption and decryption purposes.
Encryption is done by the person who is sending the data to the destination but the decryption is done at the person who is receiving the data. In asymmetric or public key encryption there are two keys. Encryption is a process of converting normal data into an unreadable form whereas Decryption is a method of converting the unreadablecoded data into its original form.
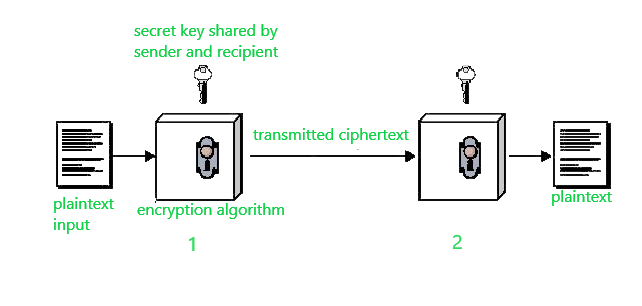
Both sender and receiver agree upon a secrete key to be used in encrypting and decrypting. Conventional Encryption also referred to as symmetric encryption or single-key encryption was the only type of encryption in use prior to the introduction of public-key encryption in the late 1970s. In public key encryption the sender and the receiver use different keys.
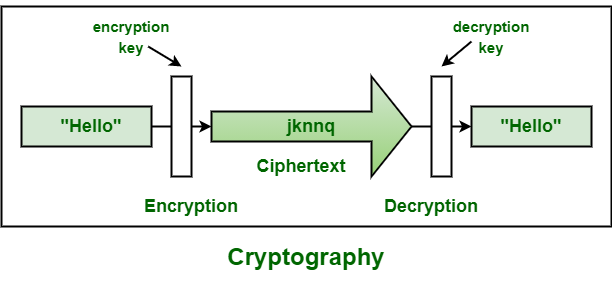
Encryption is the process of converting plain text into ciphertext ie converting the text from readable format to non-readable format to secure the conversation between two parties or from the unauthorized person. Symmetric encryption is also referred to as conventional encryption or single-key encryptionIt was the only type of encryption in use prior to the development of public-key encryption. Up to 24 cash back Symmetric single key secret key or conventional encryption.
A conventional encryption scheme has five ingredients. Usually the secrete key is transmitted via public key encryption methods. In this encryption model the sender encrypts the plaintext using the receivers secret key which can be later used by the receiver to.
Conventional encryption is a cryptographic system that uses the same key used by the sender to encrypt the message and by the receiver to decrypt the message. In secret key encryption every bit added doubles on average the time taken to break a piece of encrypted information breaking is a term used to describe recovering encrypted information. T or F The strength of a hash function against brute-force attacks depends solely on the length of the hash code produced by the algorithm.
In this encryption method both the sender and the receiver use the same single key. Conventional encryption ciphers rely on a single key for both encryption and decryption. However this advancement in technology has also exposed a potential limitation of todays encryption methods.
Encryption is the process of converting plain text into cipher text ie. The good news is that the encryption software market is growing. Encryption is one of the most widely used and successful data protection technologies in todays corporate world.
Data that has not been encrypted is referred to as plaintext and data that has been encrypted is referred to as ciphertext. The complexity of encryption methods has been successively increasing ever since. Conventional Encryption involves transforming plaintext messages into ciphertext messages that are to be decrypted only by the intended receiver.
In conventional encryption methods the encryption and decryption keys are same and secret. Symmetric Encryption Conventional cryptography also known as conventional encryption is the technique in which only one key is used for both encryption and decryption. That research suggests that if your enterprise fails to prioritize encryption it could lag compared to competitors.
Terms in this set 30 1. As computing power increased over the years encryption technology has only become more advanced and secure. Encryption is a critical tool for maintaining data integrity and its importance cannot be overstated.
Public key algorithms are useful in the exchange of conventional encryption keys. The key algorithmic ingredients of _____ CCM _____ are the AES encryption algorithm the CTR mode of operation and the CMAC authentication algorithm. The basic idea is that one performs encryption for multimedia content in a way that only a certain amount of perceptual information is touched by the encryption.
Conventional encryption also referred to as symmetric encryption or single-key encryption is a cryptographic system which uses the same key used by the sender to encrypt the message and by the receiver to decrypt the message. Slightly less 42 mentioned having a limited encryption strategy used for certain applications or types of data. Character level encryption and Bit level Encryption.
On the other hand Decryption is the process of converting ciphertext into plain text ie.

What Types Of Encryption Are There Ico
Conventional Encryption Geeksforgeeks
Difference Between Encryption And Cryptography Geeksforgeeks
0 Response to "Conventional Encryption Is a Term Used to Describe ______________ Encryption"
Post a Comment